Archive Response to Azure Storage Policy
Custom Policy Example
Zuplo is extensible, so we don't have a built-in policy for Archive Response to Azure Storage, instead we've a template here that shows you how you can use your superpower (code) to achieve your goals. To learn more about custom policies see the documentation.
In this example shows how you can archive the body of outgoing responses to Azure Blob Storage. This can be useful for auditing, logging, or archival scenarios.
modules/my-policy.ts
Configuration
The example below shows how to configure a custom code policy in the 'policies.json' document that utilizes the above example policy code.
config/policies.json
Policy Configuration
name<string>- The name of your policy instance. This is used as a reference in your routes.policyType<string>- The identifier of the policy. This is used by the Zuplo UI. Value should bearchive-response-azure-storage-outbound.handler.export<string>- The name of the exported type. Value should bedefault.handler.module<string>- The module containing the policy. Value should be$import(./modules/YOUR_MODULE).handler.options<object>- The options for this policy. See Policy Options below.
Policy Options
The options for this policy are specified below. All properties are optional unless specifically marked as required.
blobCreateSas<string>- The Azure shared access token with permission to write to the bucketblobContainerPath<string>- The path to the Azure blob container
Using the Policy
Using the Policy
In order to use this policy, you'll need to setup Azure storage. You'll find instructions on how to do that below.
Setup Azure
First, let's set up Azure. You'll need a container in Azure storage
(docs).
Once you have your container you'll need the URL - you can get it on the
properties tab of your container as shown below.
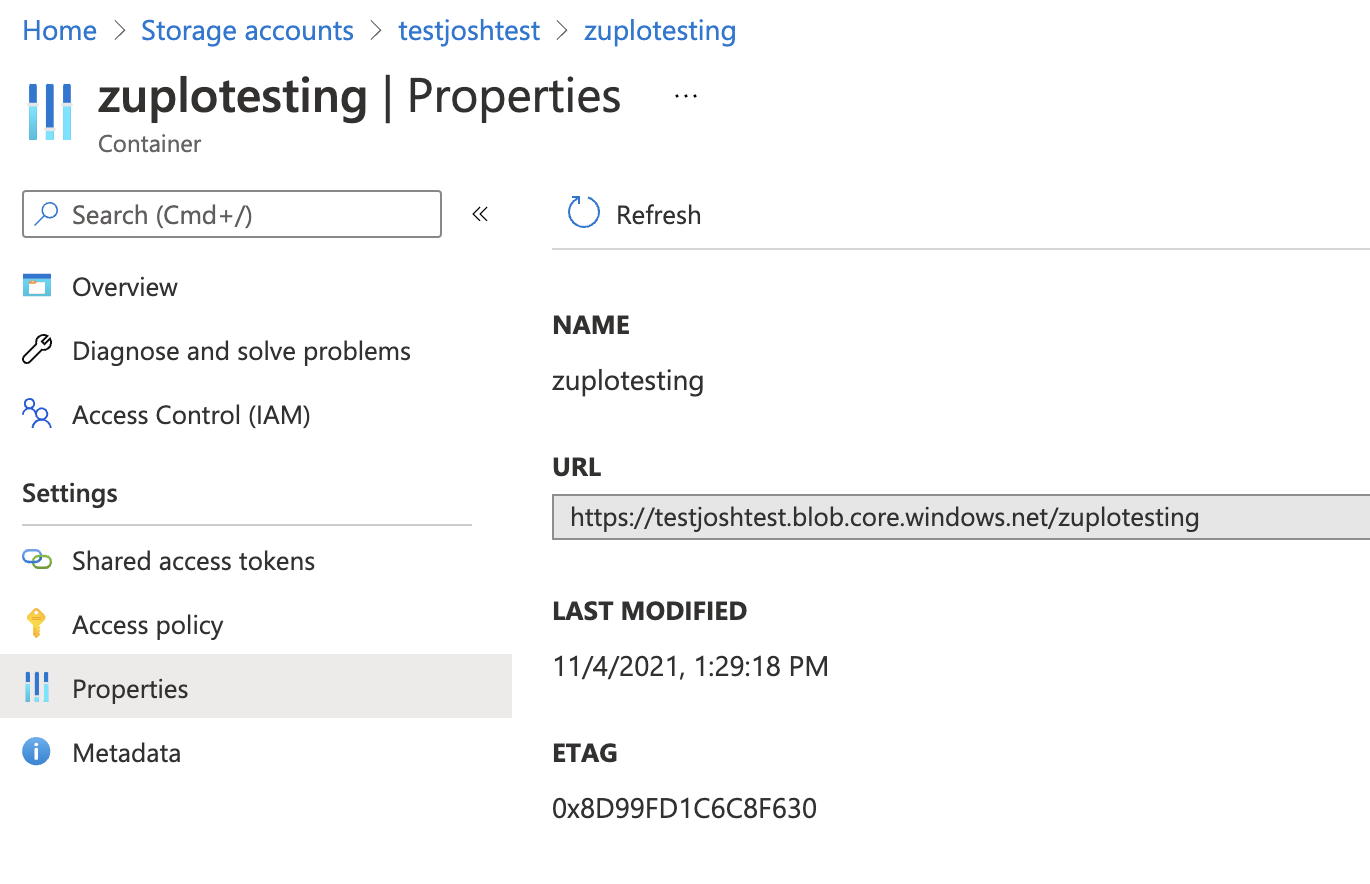
This URL will be the blobPath in our policy options.
Next, we'll need a SAS (Shared Access Secret) to authenticate with Azure. You
can generate one of these on the Shared access tokens tab.
Note, you should minimize the permissions - and select only the Create
permission. Choose a sensible start and expiration time for your token. Note, we
don't recommend restricting IP addresses because Zuplo runs at the edge in over
200 data-centers world-wide.
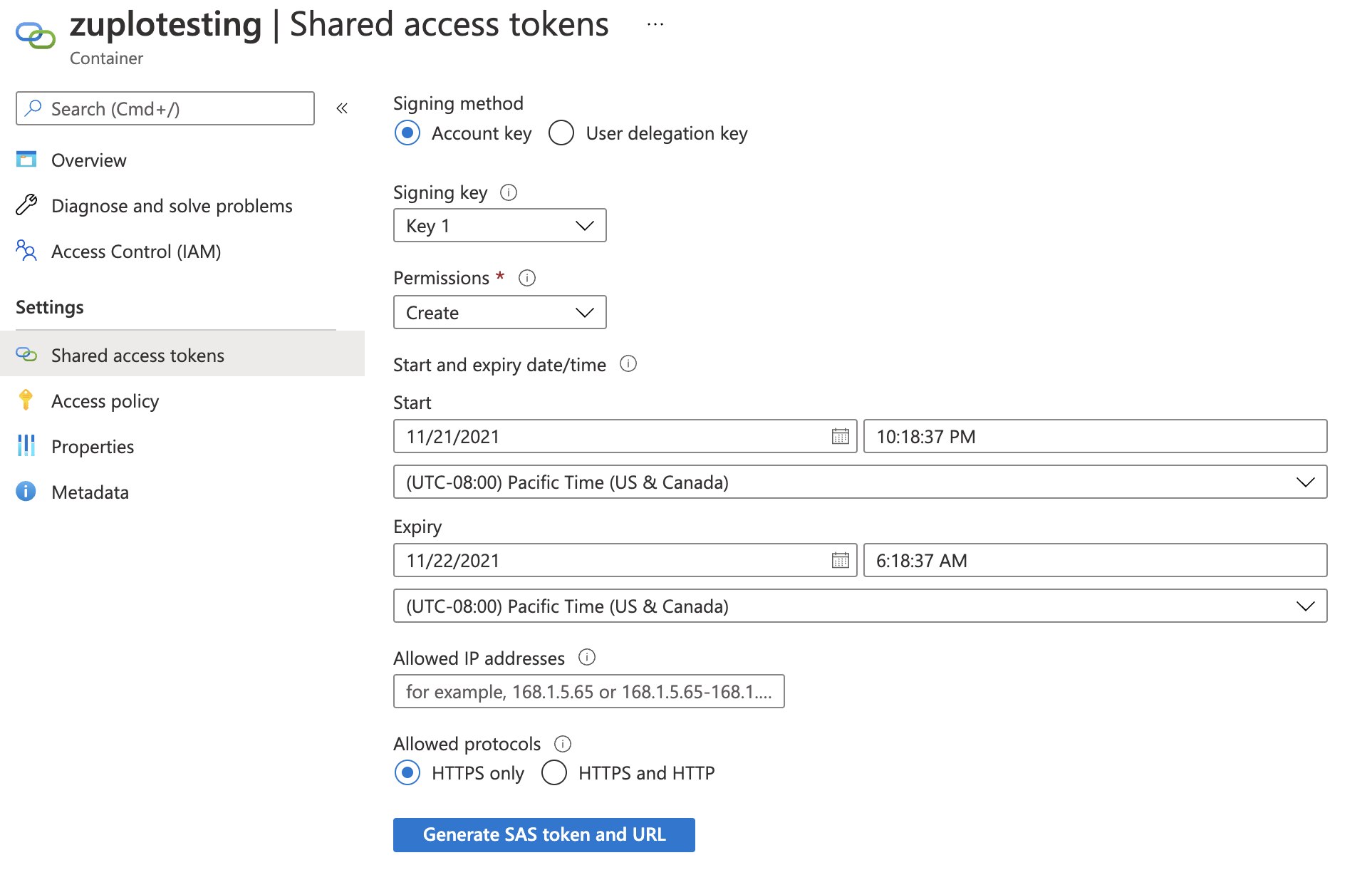
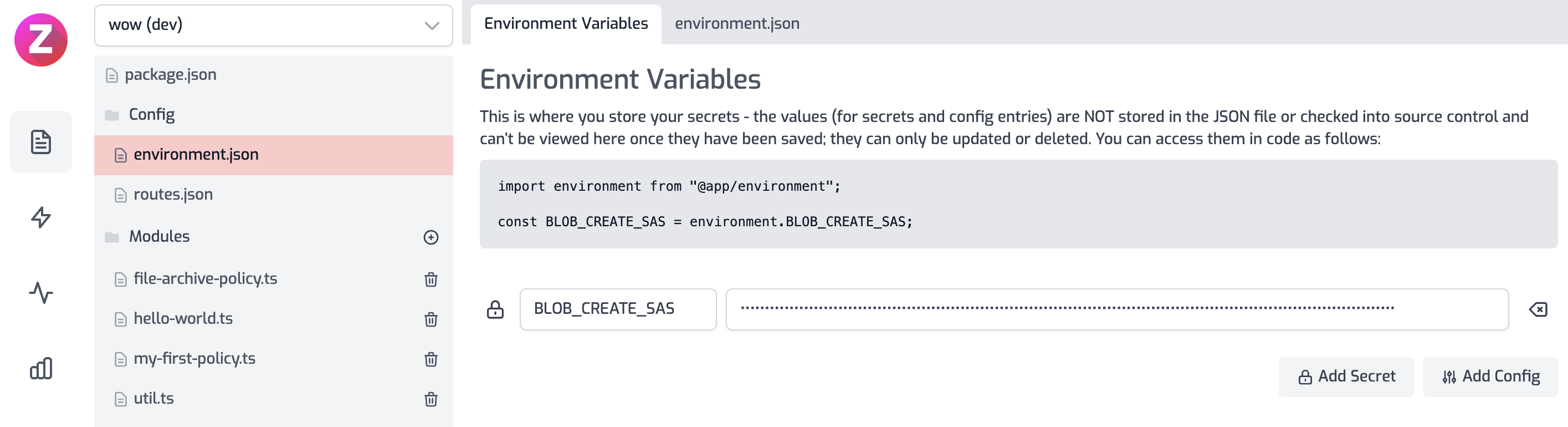
Then generate your SAS token - copy the token (not the URL) to the clipboard and
enter it into a new environment variable in your API called BLOB_CREATE_SAS.
You'll need another environment variable called BLOB_CONTAINER_PATH.
Read more about how policies work