As APIs become more essential, DDoS attacks are on the rise. These attacks work by mixing malicious traffic with legit requests, leading to performance issues like latency, timeouts, and server errors. Your server resources—bandwidth, CPU, and memory—get drained, slowing things down or even bringing your services to a halt for real users.
So how do you avoid this chaos? By implementing a flexible, scalable DDoS protection strategy that keeps your API resilient, even under heavy traffic. Here are five pro tips to level up your API security against DDoS attacks and keep things running smoothly:
- Implement Strong Authentication Mechanisms
- Deploy API Gateways for Traffic Management
- Enforce Input Validation to Filter Malicious Requests
- Monitor and Log API Activity for Anomaly Detection
- Implement a DDoS Response Plan for Swift Action
What Are DDoS Attacks?
DDoS (Distributed Denial of Service) attacks are like a flood of fake traffic sent to overwhelm your server, service, or network. The goal? To drain system resources until your API grinds to a halt. DDoS attacks come in a few different flavors:
- Volumetric attacks, which throw massive amounts of data at your system.
- Protocol attacks, which take advantage of weaknesses in network protocols.
- Application-layer attacks, which focus on exploiting vulnerabilities in your API itself.
These attacks can range from small, targeted hits to massive botnet-driven storms, affecting your service quality and potentially tarnishing your reputation. Protecting against them, therefore, is a non-negotiable.
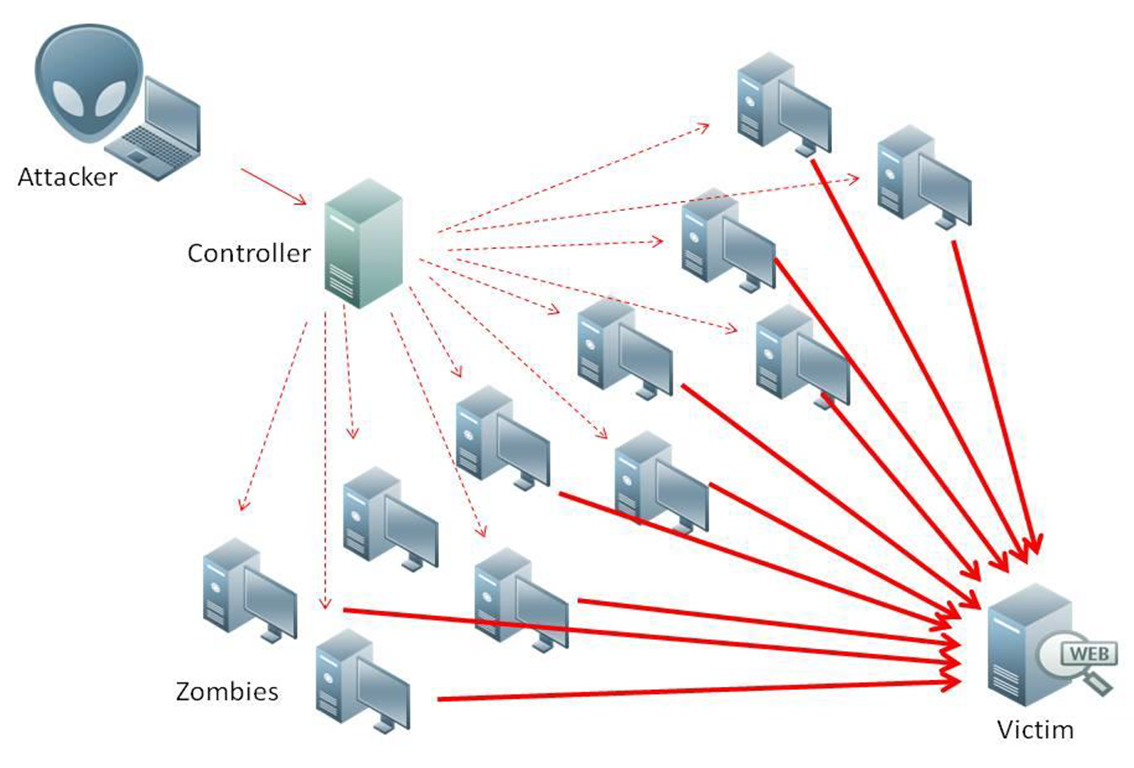
Why Do You Need Protection Against DDoS Attacks?
Prevent Service Downtime
DDoS attacks can cause your service to go offline, sometimes for an extended period. That’s a real problem, especially when users expect constant availability. Even a little downtime can annoy your users and lead to a loss of revenue. The last thing you want is for customers to go elsewhere because they couldn’t access your service when they needed it.
Maintain Consistent Performance
When DDoS attacks hit, your API is forced to deal with far more traffic than it was designed for, leading to slow response times and high latency. This makes it harder for your API to maintain a consistent user experience, especially during peak times — again, not something you want your customers to have to deal with.
Preserve Server Resources
DDoS attacks gobble up server resources like bandwidth, CPU, and memory — leaving less room for them to handle real requests. The result? Slower load times, error messages, or even system crashes. By protecting your API, you’re ensuring that it stays stable and ready to serve the people who truly need it.
Protect Your Reputation and Trust
A DDoS attack can seriously damage your reputation. Customers expect a reliable experience, and if your service is constantly going down or performing poorly, they’re going to start looking elsewhere. Protecting your API means keeping things running smoothly and ensuring your users trust you to deliver a solid experience every time.
Prevent Financial Losses
Downtime and poor performance aren’t just annoying—they’re costly. Every minute of downtime could mean lost sales, especially for e-commerce or service-based models. Plus, fighting back against a DDoS attack requires resources — IT staff, security tools, and potentially legal fees if a data breach occurs. All these add up fast, and the recovery cost can hurt your bottom line.
Ensure Regulatory Compliance
In some industries, uptime and security aren’t just "nice to haves"—they’re requirements. Financial services, healthcare, and government sectors often face strict regulations around service availability and security. A DDoS attack could leave you exposed to fines or legal issues if it violates compliance standards. With the right protection in place, you can stay on the right side of these regulations.
Stay Ahead of Evolving Threats
DDoS attacks are evolving. They’re not just large, brute-force floods anymore; modern attacks are much more sophisticated and can target multiple vectors. This means your defense strategy has to stay one step ahead. By investing in robust protection mechanisms now, you're ensuring your API can adapt to new threats and stay resilient against whatever comes next.
In short, without DDoS protection, your API is vulnerable to downtime, performance issues, and the significant costs that come with them. But don’t worry—we’ve got five tips to help you enhance your API security and keep those DDoS attackers at bay.
1. Implement Strong Authentication Mechanisms to Prevent DDoS Attacks
When it comes to defending your API against DDoS attacks, strong authentication is your first line of defense. It ensures that only legitimate users can access your services while keeping those pesky attackers at bay.
The best part? You don’t have to sacrifice performance for security. By integrating advanced authentication features and following API security best practices, you can lock things down tight without slowing everything down.
Use Multi-Factor Authentication (MFA)
Multi-factor authentication is a game-changer for access control. Instead of relying on just a password (which, let’s face it, can be easily guessed or stolen), MFA asks for a second layer of verification, like a code sent to a device or app. It’s like adding a security guard that checks your ID before letting you into the club.

Even if an attacker gets their hands on one of your user’s credentials, MFA makes it so much harder to gain access. This extra step is especially useful during DDoS attacks when attackers try to exploit every vulnerability they can find.
Leverage Token-Based Authentication to Mitigate DDoS Attacks
If you haven’t already, it’s time to embrace OAuth 2.0 or JSON Web Tokens (JWT). These tokens act as short-lived passes that verify each user request. They’re like a VIP pass that expires quickly, making it hard for malicious actors to hang around for long. By using these methods, you’re not only streamlining access but also boosting your security through secure API authentication. In the middle of a DDoS attack, token-based systems help prevent unauthorized access without skipping a beat.
So, by using things like OAuth 2.0 or JWT, you’re strengthening your defenses against attacks while keeping things smooth and efficient. It’s a win-win. Your API remains safe, your users are protected, and your systems don’t get bogged down with unnecessary slowdowns.
In short, implementing solid authentication methods is a smart move to ensure your API can fend off DDoS attacks while maintaining its performance. Plus, you’ll have peace of mind knowing you’ve got top-notch security in place.
2. Deploy API Gateways for Traffic Management Against DDoS Attacks
When it comes to keeping your APIs safe from DDoS attacks, deploying hosted API gateways is a smart move. Think of an API gateway as a traffic cop, directing and managing the flow of data while making sure that no rogue traffic gets through to overwhelm your systems. With built-in features like rate limiting and throttling, API gateways help ensure your systems stay resilient and responsive even when traffic spikes.
Centralized Traffic Management to Prevent DDoS Attacks
One of the major perks of using an API gateway is centralized traffic management. This is like having a checkpoint where all API requests go through first, and the gateway decides which ones get the green light and which malicious intruders need to be sent packing. Even better, with hosted API gateway benefits like federated gateways, you can scale up your defenses and handle more traffic efficiently.
As developers, this gives you the power to create custom traffic rules that fit your app’s specific needs. So, whether you’re under a DDoS attack or just dealing with normal traffic peaks, you can easily control the load and maintain stability. Plus, you can tweak these rules on the fly to ensure everything stays smooth.
Implement Rate Limiting and Throttling
Rate limiting and throttling are where API gateways really shine. By setting request limits per minute or hour, these features control how many requests a single client can make in a given time frame. This is key for defending against DDoS attacks, where an attacker tries to flood your system with requests. With API rate limiting, you make sure no one user can drain your resources.
Rate limiting can be as easy as setting up a simple rule or as complex as you need it to be with dynamic rate limiting. You can choose from a variety of rate-limiting strategies like Fixed Window, Sliding Window, or Token Bucket, each offering a different way to manage traffic depending on your needs. These are some of the essential API gateway features that help maintain your API's performance and security.
If a user exceeds their limits, the API signals them with a helpful HTTP 429 status code—basically saying, “Whoa there, slow down!” And here’s a bonus tip: edge computing can be your secret weapon. By processing data closer to the user, you can reduce latency and boost performance, all while maintaining high security and keeping those backend resources protected.
3. Enforce Input Validation to Filter Malicious Requests During DDoS Attacks
When it comes to defending your API, input validation is one of your first lines of defense. It’s like your personal bouncer, making sure that only well-formed, expected data gets through the door while keeping the bad actors out. Not only does input validation protect against common threats like SQL injection (SQLi) and Cross-Site Scripting (XSS), but it also helps block malicious requests during DDoS attacks. By implementing strict validation rules, you’re cutting down your API’s exposure to potential vulnerabilities.
Sanitize Inputs to Block Malicious Data
During a DDoS attack, input validation becomes even more critical. You’re not just looking for malicious traffic—you’re looking for traffic that’s trying to sneak in disguised as legitimate requests. That's where sanitizing inputs really comes into play. By filtering out harmful data before it reaches your system, you keep your APIs clean and secure.
- Prevent SQL Injection: You don’t want attackers embedding malicious code in user inputs to manipulate your database. Filter out that bad stuff and make sure only safe, well-formed data gets through.
- Block XSS Attacks: Don’t let harmful scripts hijack your users or deface your site. Input validation ensures there’s no executable code slipping through, so you can avoid that mess.
By putting these input validation techniques in place, you’re proactively filtering out threats and maintaining the integrity of your system, even in the middle of an attack.
Use OpenAPI and JSON Schema for Consistency
Want to level up your validation game? Incorporate standards like OpenAPI specifications and JSON Schema validation. These tools provide structure and consistency across your APIs, helping to automate input validation. With OpenAPI and JSON Schema, your API data has to adhere to expected formats and structures—no more malformed requests sneaking through.
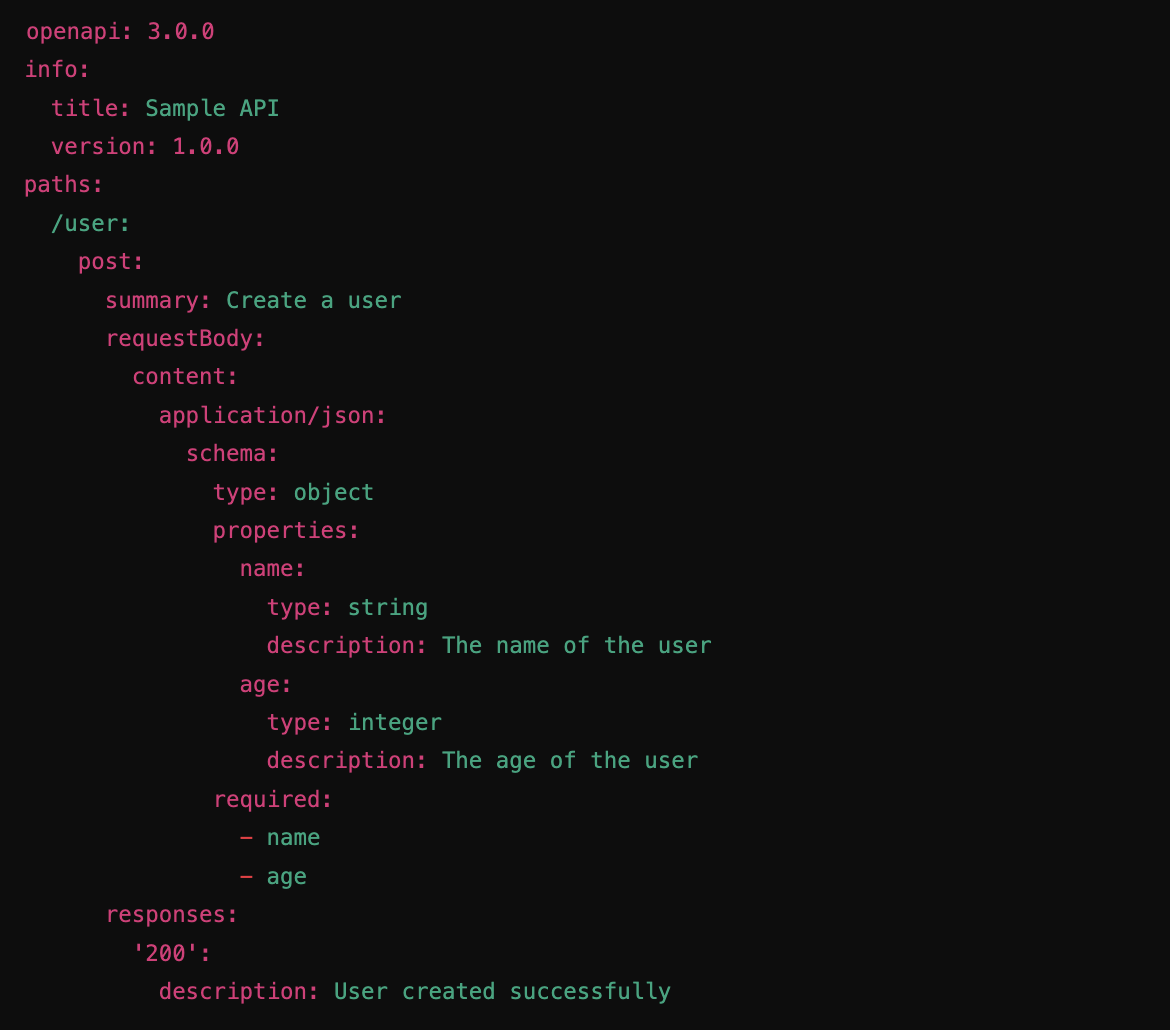
Not only does this approach make your system more secure, but it also helps you maintain clear and consistent documentation. Plus, it aligns your API security with industry best practices, making ongoing security evaluations and updates a breeze.
By diligently enforcing these input validation practices, you’re adding another layer of protection to keep your APIs secure and reliable. It’s like adding an extra level of scrutiny to your gatekeeper, ensuring only the good guys get in.
4. Monitor and Log API Activity for Anomaly Detection of DDoS Attacks
When your API is at the heart of your application, monitoring it in real-time is key to detecting potential DDoS attacks before they disrupt service. Leveraging advanced monitoring tools and comprehensive logging systems helps you spot unusual traffic patterns quickly, enabling you to mitigate threats as they emerge. With the power of edge computing, you can get insights even faster, ensuring your defenses are proactive rather than reactive.
Real-Time Monitoring for Suspicious Activity
Real-time monitoring is an essential part of any effective API security strategy. By constantly tracking traffic for unusual spikes or patterns, you can detect potential DDoS attacks before they cause damage. Modern API monitoring tools help you quickly identify suspicious activity like sudden surges or bot-driven traffic, allowing you to respond fast and block malicious requests before they impact your API. This kind of proactive monitoring is essential to maintaining API security.
With edge computing, this process becomes even more efficient. It accelerates anomaly detection by processing data closer to the source, ensuring faster response times and reducing latency during traffic analysis.
Enable Comprehensive Logging for Better Response
Detailed logging is crucial for understanding the specifics of any attack. By keeping track of every request and its associated data, you can quickly pinpoint abnormal behavior and respond with precision. Detailed logs allow your team to trace the origin of suspicious traffic, identify patterns, and adjust defenses to prevent future incidents.
By combining real-time monitoring with in-depth logging, you create a robust system that can detect, analyze, and react to potential DDoS threats more effectively—keeping your API secure and your users happy.
5. Implement a DDoS Response Plan for DDoS Attacks
When DDoS attacks come knocking, a well-prepared response plan helps you protect your digital assets, minimize downtime, and keep things running smoothly. Think of it as having a game plan for when things go sideways—because when a DDoS attack hits, you don’t want to be scrambling for answers.
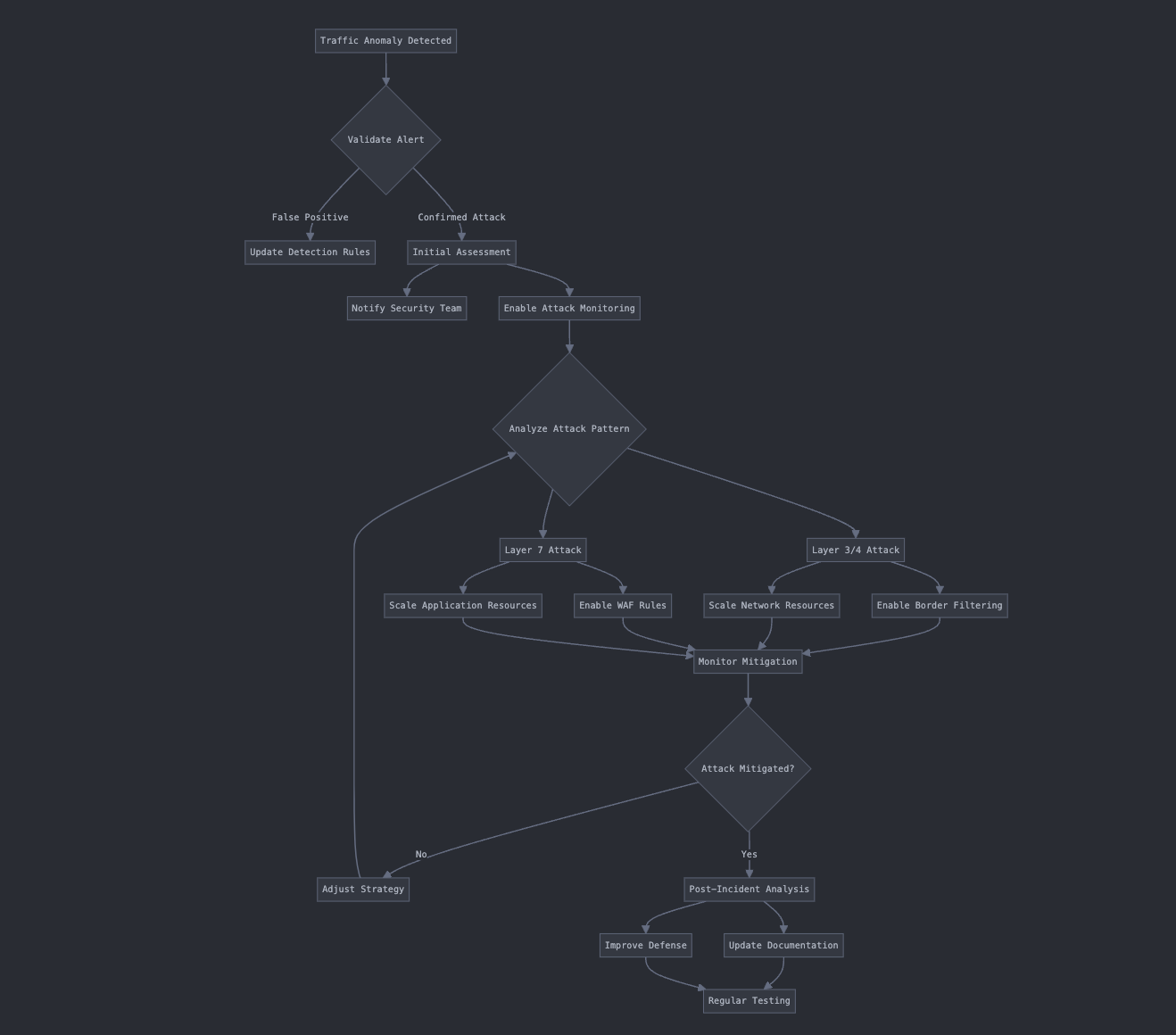
Define Clear Roles and Responsibilities
A successful DDoS response starts with a clearly defined team structure. Everyone needs to know their role, from network admins to company leaders, so when the attack hits, everyone can jump into action without hesitation. Customizable platforms can help IT teams implement countermeasures based on predefined rules, ensuring that your response is both quick and effective.
Perform Regular DDoS Drills
Planning is just the start. To truly be ready for an attack, you need regular practice. DDoS drills help your team get comfortable with the process, identify any weak spots, and fine-tune your response plan. The beauty of flexible platforms is that they let you adjust configurations on the fly, so your infrastructure can adapt to new attack techniques. This ensures you stay ahead of increasingly sophisticated threats, ready for whatever comes next.
By setting up a solid DDoS response plan and keeping it fresh with regular drills, you make sure your team is always prepared to defend your critical services and minimize disruptions—no matter what the digital world throws your way.
The Final Step to Defend Against DDoS
Maximizing API throughput is key to keeping things running smoothly, especially when the pressure’s on. By fine-tuning your endpoints, caching like a pro, using asynchronous processing, and implementing strategies such as connection pooling and data compression, you can make your API lean, mean, and lightning-fast. These practices reduce latency, handle more traffic, and keep everything flowing even during peak demand.
When you invest in optimizing your API, you're setting it up for long-term success. Your users get the seamless experience they expect, and your API can scale gracefully as traffic grows. Ready to take your API throughput to the next level? Dive into how Zuplo’s flexible, scalable platform can help you implement these strategies and boost your API performance. Get started with Zuplo today!