Developers often find themselves building an amazing API when suddenly hitting the security question. How to keep things locked down without making life miserable for users? That's where OAuth 2.0 comes in. It's become the gold standard for API security, and for good reason. It provides this flexible framework that protects resources while actually creating a decent experience for users. No small feat!
OAuth 2.0 tosses the old credential-sharing approach in the trash where it belongs, enabling secure, limited access through a clever token system. It’s kind of like having a valet key for a car—it lets someone park the vehicle without giving them access to the glove compartment, trunk, or ability to take it on a cross-country road trip.
Let's dive into how OAuth 2.0 works, why it matters for API strategy, and how to implement it without pulling out hair (while building trust with developers and users along the way).
- OAuth 2.0 Fundamentals: The Players and Tokens
- Choosing the Right Grant Type For Your Use Case
- Confidential vs. Public Clients: Making the Right Choice
- Implementation Guide: Best Practices for Real-World OAuth
- Troubleshooting Common OAuth Issues
- Looking Forward: OAuth 2.1 and Emerging Standards
- Keep Your APIs Safer Than Houses
OAuth 2.0 Fundamentals: The Players and Tokens
Getting started with OAuth 2.0 requires understanding what makes it tick. This framework changed the API security game through one brilliantly simple idea—separating authentication from authorization.
OAuth 2.0 sets up a security model with four main players (think heist movie with specialized roles):
- Resource Owner: The end-user who actually owns the data. They're the ones clicking that "Allow" button when some app asks for permission.
- Client: The application trying to access resources. Could be a mobile app, web application, or service that wants access to user data.
- Authorization Server: The bouncer at the club who checks IDs, ensures everyone knows what they're agreeing to, and hands out the VIP wristbands (tokens).
- Resource Server: The actual API that holds all the valuable data, constantly checking tokens before serving resources.
Keeping these roles separate creates layers of security that are tough to break through.
The Token System That Powers Everything
At the heart of OAuth 2.0 is its token-based approach, which means passwords no longer need to be passed around like hot potatoes:
- Access Tokens – These are temporary passes to the API kingdom. They typically expire in hours (sometimes minutes) and carry specific permissions. Think of them as those visitor badges that change color after 24 hours so security knows they're expired. They're meant to be short-lived for a reason—if someone steals one, they can only cause trouble for a limited time.
- Refresh Tokens – These are the longer-lived credentials that let apps get new access tokens without bugging the user for their password again. They're like having a relationship with the building security guard—no need to go through the whole visitor registration process every morning; just wave and get a new daily badge.
- Scopes – This is OAuth's way of saying "enter the kitchen and bathroom, but stay out of the bedroom and office." OAuth Scopes define exactly what permissions an application has—maybe it can read emails but not send them, or view a profile but not change it. They're the antidote to the all-or-nothing access model that plagued earlier auth systems.
Choosing the Right Grant Type For Your Use Case
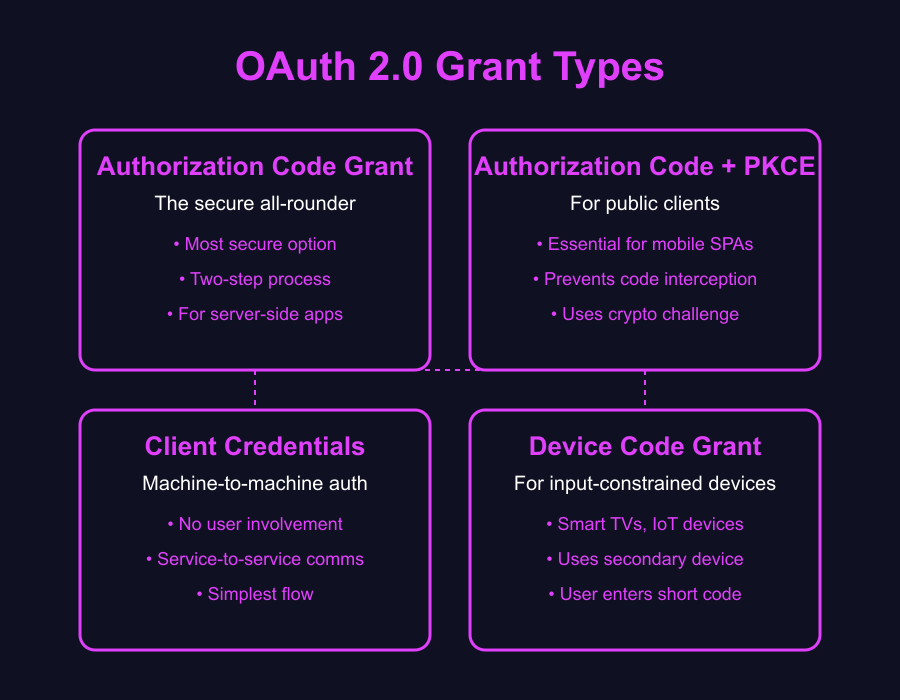
OAuth 2.0 isn't a one-size-fits-all solution. It offers several specialized "grant types" tailored for different scenarios. Picking the right one is crucial for balancing security and usability.
Think of grant types like different tools in a security toolbox. No one would use a sledgehammer to hang a picture. Same idea here. Let's break down the most common ones and when to reach for each.
Authorization Code Grant: The Secure All-Rounder
The Authorization Code grant is the Swiss Army knife of OAuth—it's the most widely used and secure option for good reason. Instead of handing out access tokens directly (which would be risky), it uses a two-step dance: first, get a temporary code, then swap that code for the actual tokens.
This grant type is ideal when:
- Building a server-side web application where secrets can be hidden
- Needing serious security because of handling sensitive data
- The application can keep secrets better than a five-year-old with a surprise birthday present (meaning: it can keep client secrets confidential)
Here's how it works:
# Step 1: Redirect user to authorization URL
PKCE: Essential Security for Mobile and SPAs
PKCE (pronounced "pixie"—yes, really) is like the Authorization Code grant's bodyguard. It extends the basic flow with an extra layer of protection that's perfect for apps that can't keep secrets. It prevents those nasty authorization code interception attacks by using a fancy cryptographic challenge that proves the app requesting the token is the same one that started the flow.
PKCE becomes essential when:
- Building mobile applications where code can be decompiled and secrets extracted
- Creating single-page applications (SPAs) where all code runs in the browser
- Working with any client that's about as good at keeping secrets as a gossip columnist (meaning: can't securely store a client secret)
Here's a JavaScript implementation example:
Client Credentials: Streamlining Service-to-Service Auth
The Client Credentials grant is OAuth stripped down to its essentials—perfect for when machines need to talk to machines without any humans in the mix. No redirects, no user consent screens, just direct service-to-service communication. It's OAuth at its most businesslike and efficient.
This grant type is ideal when building:
- Microservices that need to securely chat with each other
- Background jobs and cron processes that run when users are asleep
- API-to-API integrations where there's no user sitting at a keyboard
The flow is straightforward:
Device Code: Solving the Input-Constrained Problem
The Device Code grant is designed specifically for devices with limited input capabilities, like smart TVs or IoT devices, where entering credentials is challenging.
Use this when:
- Building for smart TVs or streaming devices
- Creating applications for IoT devices
- Working with CLI applications where browser auth is inconvenient
The process works through a secondary device:
Confidential vs. Public Clients: Making the Right Choice
Not all apps are created equal when it comes to keeping secrets. Some are like Fort Knox, while others are more like a sticky note on a monitor. OAuth 2.0 acknowledges this reality by splitting clients into two camps: confidential and public. Knowing which is which can make or break a security setup.
This isn't just some technical footnote—choosing between these client types is a fork-in-the-road moment that shapes the entire OAuth implementation. Getting it wrong is like leaving the front door unlocked with a "Please Take My Data" sign.
Confidential Clients: When Security Is Paramount
Confidential clients can securely store authentication credentials without exposing them. These are typically server-side applications where code and secrets are protected from end users.
Key characteristics include:
- Ability to keep client secrets confidential
- Running on secure servers with protected code
- Access to secure storage mechanisms
- Implementation of proper safeguards against credential leakage
Examples of confidential clients include:
- Traditional web applications with server-side components
- Backend services and APIs
- Enterprise applications running in controlled environments
Public Clients: Handling the Security Challenge
Public clients cannot maintain the confidentiality of client secrets. These are typically applications where the code runs on a user's device and could potentially be inspected.
Their defining features include:
- Inability to securely store client secrets
- Running on the user's device
- Code that can be inspected or decompiled
- Higher risk of credential extraction
Common examples include:
- Single-page applications (SPAs)
- Native mobile applications
- Desktop applications
- Browser extensions
Making Your Decision
When deciding which client type to implement, consider these factors:
- Application Architecture: If the application has server-side components where secrets can be securely stored, a confidential client makes sense. For pure client-side applications, a public client approach is necessary.
- Security Requirements: Applications handling sensitive data should use confidential clients when possible due to their stronger security properties.
- User Experience: Consider how the authentication flow will impact users' experience. Sometimes, the trade-off between perfect security and a smooth user experience needs careful consideration.
- Grant Flow Requirements: If using the Client Credentials grant (for server-to-server communication), a confidential client is required. Public clients are typically limited to the Authorization Code grant with PKCE.
Making the right choice here establishes the foundation for the entire OAuth implementation strategy.
Implementation Guide: Best Practices for Real-World OAuth
After picking a grant type and client model, is the system totally secure? Not so fast. Even with the perfect OAuth 2.0 configuration, security holes can pop up faster than moles in a whack-a-mole game if implementation details aren't carefully managed. The theory is important, but real-world implementation requires both security awareness and practical knowledge suited to each environment.
The Security Foundation: Non-Negotiable Practices
RFC 9700 serves as the security bible for OAuth implementations, representing years of hard-won lessons turned into actionable advice. These core practices aren't optional—they're essential for any secure OAuth implementation:
- Always Use HTTPS for all OAuth-related traffic. Tokens transmitted over plain HTTP are essentially public information.
- Implement Token Binding through techniques like mTLS or DPoP to prevent stolen tokens from being used by attackers.
- Validate All Inputs rigorously, especially redirect URIs, to prevent injection attacks and open redirects.
- Use State Parameters to prevent cross-site request forgery (CSRF) attacks:
- Limit Token Lifetimes to minutes or hours rather than days or weeks, minimizing the damage potential of compromised tokens.
Server-Side Applications: The Confidential Client Path
Traditional web applications offer the most secure implementation path. With server-side code hidden from users, these apps can safely implement the Authorization Code flow with a confidential client approach.
The implementation path follows a clean sequence: registering with an OAuth provider, initiating the authorization with careful parameter validation, securely processing the response, and properly managing token lifecycle. The key advantage here is that tokens never reach the browser, remaining protected on the server.
Most frameworks offer OAuth libraries that handle the heavy lifting. Django's
social-auth, Rails' omniauth, and Express.js's passport all provide
well-tested implementations. These libraries manage the complexity while
offering customization points for specific needs.
Browser-Based Applications: Securing the Insecure
Single-page applications present unique challenges since all code runs in the browser. The traditional solution—the Implicit flow—has been deprecated due to security concerns. Today's approach relies on the Authorization Code flow with PKCE, creating a substantially more secure model.
Implementing OAuth in SPAs requires careful attention to token storage. Access tokens should ideally remain only in memory, while refresh tokens can be stored as HttpOnly cookies with appropriate protections. The goal is keeping tokens inaccessible to JavaScript, protecting against XSS attacks.
Token renewal presents another challenge. Silent refresh techniques using hidden iframes work well for many identity providers, while others require more complex approaches. The key security principle remains consistent: never expose refresh tokens to JavaScript.
Mobile Applications: Unique Devices, Unique Challenges
Mobile environments present their own security landscape. The primary risks include code decompilation, insecure storage, and malicious apps intercepting redirects. A robust implementation addresses each concern specifically.
- Secure the Authentication Flow: Always use the system browser or specialized authentication sessions rather than embedded WebViews. This approach leverages the security features of the platform's browser and separates the authentication context from the application.
- Protect Sensitive Data: Use platform-specific secure storage mechanisms (iOS Keychain, Android EncryptedSharedPreferences) rather than standard preferences or local storage. These mechanisms handle encryption and secure storage details that would be challenging to implement correctly from scratch.
- Safeguard the Redirection Process: Leverage App Links (Android) or Universal Links (iOS) to create secure redirect pathways that resist interception from malicious applications. Proper verification of incoming redirect data is essential before processing.
Troubleshooting Common OAuth Issues
Even with proper implementation, OAuth integrations can be finicky. One small misconfiguration can result in cryptic error messages and locked-out users. Understanding common issues and their solutions helps navigate the troubleshooting process more efficiently.
Authentication and Authorization Failures
The path from user authentication to successful API access has several potential breaking points:
- Redirect URI Mismatch Errors: This infamous error occurs when the redirect
URI in the authorization request doesn't exactly match one registered with the
OAuth provider. Even trailing slashes matter -
https://app.com/callbackandhttps://app.com/callback/are considered different URIs. Always check the registered URIs in the provider's console and ensure exact matches in requests. - Invalid Scope Errors: Authorization may fail if requesting scopes that are unavailable or require additional permissions. Start with minimal scopes to isolate issues, and verify the application has permission to request all scopes in the authorization request.
- CSRF Vulnerabilities: Without proper state parameter implementation, attackers can trick users into executing unwanted authorization requests. If users report unexpected authorization prompts, check for missing or improperly validated state parameters.
Token Management Challenges
Several common errors appear during token issuance, validation, and refresh:
- Invalid Client Errors: The dreaded "invalid_client" message typically points to incorrect OAuth credentials. Double-check client IDs and secrets, especially when moving between environments. Development credentials won't work in production.
- Token Validation Failures: Resource servers may reject seemingly valid tokens for various reasons. Check expiration times, audience claims, and scope restrictions. Even properly obtained tokens will be rejected if they lack the necessary permissions for the requested action.
- Refresh Token Issues: The "invalid_grant" error frequently appears when refreshing tokens, indicating the refresh token has expired, been revoked, or was already used. Implement proper refresh token rotation and monitor token lifetimes carefully.
Platform-Specific Obstacles
Different implementation environments face unique challenges:
- CORS Issues in SPAs: Single-page applications often hit Cross-Origin Resource Sharing restrictions when making token requests. Configure appropriate CORS headers on the authorization server or use a backend proxy to handle token exchanges.
- PKCE Implementation Errors: When PKCE fails, check that the code challenge method matches what the server expects (usually S256) and verify the code verifier used for exchange matches the one used to generate the challenge.
- Mobile Browser Compatibility: Mobile apps frequently encounter "disallowed_useragent" errors when using embedded webviews. Always use the system browser or dedicated authentication libraries like AppAuth for mobile implementation.
- Session Management Problems: Browser-based apps may lose token state during page reloads. Use appropriate browser storage based on security requirements and implement silent refresh mechanisms that work across page refreshes.
When standard solutions don't resolve an issue, check the OAuth provider's documentation for specific error codes and troubleshooting guidance. Most providers offer detailed logs that can pinpoint the exact cause of authentication or token failures.
Looking Forward: OAuth 2.1 and Emerging Standards
Just when OAuth 2.0 seems all figured out, the landscape shifts again! But don't throw hands up just yet. The evolution of OAuth standards isn't about making life harder—it's about patching security holes and adapting to new tech realities. Keeping an eye on these changes helps avoid the dreaded "complete security overhaul" down the road.
OAuth 2.1 is the next big thing on the horizon. Currently in draft form, it's not a revolutionary change but more like OAuth 2.0's sensible older sibling who learned from all the family mistakes. It rolls up years of "you really shouldn't do that" advice into formal requirements.
What's New in OAuth 2.1
OAuth 2.1 introduces several important changes designed to enhance security:
- Mandatory PKCE: All clients using the authorization code flow must implement PKCE, eliminating a whole class of potential attacks.
- Removal of the Implicit Flow: This flow has been deprecated due to security vulnerabilities and is replaced by the Authorization Code flow with PKCE for browser-based applications.
- Strict Redirect URI Matching: OAuth 2.1 requires exact matching, eliminating risks associated with flexible matching.
- Enhanced Refresh Token Security: Refresh tokens must be either sender-constrained or single-use, reducing risks if tokens are compromised.
- Prohibition of Bearer Tokens in URLs: Tokens must be sent in headers or POST body parameters to prevent exposure in logs and browser history.
- These changes simplify implementation by standardizing best practices while enhancing security across all OAuth deployments.
Beyond OAuth 2.1
Looking further ahead, several developments are shaping the future of API authentication:
- Grant Negotiation and Authorization Protocol (GNAP): This next-generation authorization protocol reimagines OAuth from the ground up. It covers similar use cases but addresses more complex scenarios and removes the backward compatibility constraints.
- Decentralized Identity: Emerging standards are exploring ways to give users more control over their digital identities, potentially reducing reliance on centralized identity providers.
- Continuous Authentication: Moving beyond the traditional token model, continuous authentication approaches dynamically adjust trust levels based on ongoing behavioral analysis.
- Enhanced Security Features: Additional security measures like Pushed Authorization Requests (PAR) and hardened token binding mechanisms continue to strengthen the OAuth ecosystem.
By staying informed about these emerging standards, developers can ensure their authentication systems remain both secure and user-friendly as technology evolves.
Keep Your APIs Safer Than Houses
Setting up OAuth 2.0 for APIs isn't just ticking off some compliance checkbox—it's building a foundation of trust that users and partner developers will actually appreciate. OAuth 2.0 offers that rare combination of strong security and decent user experience (usually, one must pick just one!).
Zuplo makes implementing robust OAuth 2.0 for APIs surprisingly painless, with developer-friendly tools that handle authentication flows and token validation without the usual headaches. Sign up for a Zuplo account today and build APIs with authentication that developers will love.